If you own the Galaxy Nexus, Nexus 4, or the Nexus 5, watch out! an SMS vulnerability has been discovered on the Nexus 5 line of smartphones. It seems that this vulnerability is a bug on Android, but it does not seem to affect any other smartphone running Android. The vulnerability was discovered at the DefCamp Security Conference in Bucharest, Romania, and the person responsible for the discovery was Bogdan Alecu, a system administrator at Levi9 and independent security researcher in Romania. When exploited, the attack can force the phone to reboot or destabilize certain services.
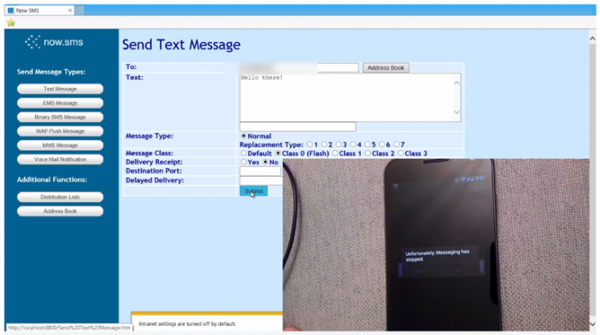
The method of attack is quite simple, actually. It relies on sending a series of Class 0 “Flash” messages to the target phone. In this case, the Nexus series. But firstly, what is a class 0 flash message?
What is a “flash message”?
Flash messages are typically used for emergency or security purposes, appearing on the screen immediately instead of going to the default SMS application. When such a message arrives, no sounds are made but the background is dimmed and a single dialog box appears on top. Once 20-30 messages pile up, assuming the user isn’t clearing them, it overloads the system and leads to a few potential side-effects. Most commonly, the result is an unresponsive device or an immediate reboot, but the Messages app or cellular radio may occasionally crash or freeze up in some instances.
In the event that the cellular radio crashes, it may have some more serious consequences. If a target has their SIM locked with a PIN code, the phone will not be able to reconnect until the code is entered. From time to time, it’s also possible for the cellular radio to seize up, which can only be fixed by restarting the device. This is problematic because there are no audible prompts and the malfunction won’t be seen until the owner unlocks their screen, leaving them without service for potentially several hours.
It seems that Bogdan Alecu already notified the Android Security Team to this particular issue over a year ago, but only received automated responses. After a few more continuous tries, he was unsuccessful, leading him to take a decision of disclosing the vulnerability publicly. To eradicate potential threats, he collaborated with Michael Mueller to develop Class0Firewall, an app designed to protect from Class 0 messages.
Bogdan also notes that the current attack is only capable of destabilizing a phone, but theorizes that it might be possible to force code execution. Hopefully the publicity will prompt Google to release a patch to block the issue ASAP.
 TechDomino
TechDomino